A data breach response plan is essentially your playbook for when things go wrong. It's a formal strategy that details exactly how your business will spot, shut down, and recover from a security incident. Think of it less as a dry IT document and more as a critical business continuity tool. It clearly defines who does what, how you communicate, and what your legal obligations are, all with the goal of minimizing the damage.
Why a Response Plan Is Non-Negotiable

Let's be blunt鈥攁 data security incident isn't a matter of if, but when. Believing your business is too small to be a target or too secure to be breached is a dangerous assumption. In reality, getting caught without a plan can turn a manageable crisis into a catastrophe that causes lasting, sometimes irreversible, harm.
The fallout goes way beyond a temporary system outage. It sends shockwaves through every corner of your organization, from daily operations right down to your bottom line.
The True Cost of Being Unprepared
The immediate financial hit is what usually grabs headlines. The average global cost of a data breach has crept up to around $4.88 million, a hefty 10% jump in just one year. For high-risk sectors like healthcare, that number is even more eye-watering, averaging a staggering $9.77 million per incident. That鈥檚 more than a 53% spike since the pandemic began, showing just how fast the financial risks are climbing.
But beyond the fines and recovery costs, the intangible damage can be even worse. The erosion of customer trust acts like a slow poison. Once it's gone, it's incredibly difficult to win back, often leading to customer churn and a long-term hit to your revenue.
A well-rehearsed plan is your organization's muscle memory in a crisis. It replaces panic with process, ensuring decisive action when every second counts. Without it, you're just improvising during a high-stakes emergency.
Moving from Reaction to Readiness
Having a solid data breach response plan flips your posture from reactive to proactive. Instead of your team scrambling to figure out who to call or what the first step is, they have a clear playbook to follow. This state of readiness gives you a few major advantages:
- Minimizes Disruption: A clear plan helps you contain a threat faster, which means less system downtime and operational chaos.
- Ensures Legal Compliance: It lays out the necessary steps for notifying authorities and affected individuals, helping you hit strict regulatory deadlines under laws like GDPR or CCPA.
- Protects Your Reputation: A transparent, organized response shows you're competent and can go a long way in preserving the trust you鈥檝e worked so hard to build with customers and partners.
Thinking through these nightmare scenarios before they happen is absolutely essential. To get a deeper dive into the nuts and bolts of preparing for an incident, this is an excellent resource. It provides a detailed roadmap for creating a plan that actually works under pressure, ensuring you鈥檙e ready for the inevitable.
Building Your Incident Response Team

Let's be blunt: a data breach response plan on paper is useless without the right people ready to execute it. When a crisis hits, you don鈥檛 have time to figure out who鈥檚 in charge or what everyone鈥檚 supposed to be doing. This is where your dedicated incident response team comes in鈥攖hey are your rapid-response unit for navigating the chaos.
Think of it less like filling out an org chart and more like casting the right experts for very specific roles. You need a mix of technical skill, legal savvy, sharp communication, and decisive leadership. Without this crew in place, even the best-laid plans fall apart under pressure, leading to confusion, delays, and a much bigger mess.
Assembling Your Core Responders
First things first, you have to identify who absolutely needs to be in the room when an incident is declared. This isn't about grabbing department heads at random; it's about assigning clear responsibilities based on expertise. Your core group should be a cross-functional team that can tackle the breach from every angle, all at once.
Picture this: ransomware just locked up your entire customer database. Your IT lead is scrambling to isolate infected systems, but who has the authority to decide if you pay the ransom? Who is crafting the message to thousands of anxious customers? And who鈥檚 keeping an eye on the clock to make sure you hit that 72-hour GDPR reporting deadline?
Each of those questions requires a different specialist. A well-built team ensures these critical actions happen in parallel, not in a panicked, one-after-the-other scramble. It turns a potential catastrophe into a managed incident.
In the heat of a breach, clarity is your greatest asset. A predefined team with crystal-clear roles eliminates the 'What now?' moment, allowing for immediate, coordinated action that can drastically reduce the overall impact.
There are four pillars to any solid response team, whether you鈥檙e a startup or a global enterprise. Each one is non-negotiable.
- Technical Experts: These are your digital first responders. Your IT and security pros are on the front lines, responsible for finding the threat, kicking it out, and cleaning up the damage.
- Legal Counsel: With the maze of breach notification laws out there, this role is absolutely critical. They provide the guardrails, advising on compliance, liability, and regulatory communication.
- Communications Lead: This is your storyteller. Your PR or communications specialist owns the narrative, managing all messaging to employees, customers, regulators, and potentially the media.
- Executive Leadership: You need someone with the final say. This person has the authority to approve major actions, like taking a system offline or allocating emergency funds to fix the problem.
Mapping Roles to Responsibilities
Once you know who should be on the team, you need to spell out what they do. Ambiguity is your enemy during a crisis. The table below gives you a practical framework for assigning these duties so there's zero confusion when things go sideways.
A well-defined set of roles and responsibilities is the backbone of an effective response. It ensures that every critical task鈥攆rom technical containment to legal reporting鈥攊s owned by a designated expert.
Key Roles in Your Data Breach Response Team
| Role | Primary Responsibilities | Essential Skills |
|---|---|---|
| Incident Commander | Oversees the entire response, coordinates all team efforts, and makes final executive decisions. | Decisive leadership, clear communication, ability to stay calm under extreme pressure. |
| Technical Lead | Manages the hands-on technical response including investigation, containment, and system recovery. | Deep knowledge of network security, forensics, malware analysis, and system architecture. |
| Legal Counsel | Advises on all legal obligations, including regulatory notifications and potential litigation risks. | Expertise in data privacy laws (e.g., GDPR, CCPA), cyber law, and compliance requirements. |
| Communications Lead | Develops and executes the communication strategy for all stakeholders, both internal and external. | Crisis communication, public relations, excellent writing skills, and media relations experience. |
This structure ensures that actions are swift and coordinated, minimizing the operational and reputational damage of a breach.
For smaller businesses, it鈥檚 common for one person to wear multiple hats. That鈥檚 perfectly fine, but it makes documenting their specific responsibilities even more important. Getting the legal piece right is especially crucial, as a misstep there can lead to massive fines. To get a better handle on what you need, you can learn more about legal help for small business and ensure you have the right expertise on call.
Building this team is a foundational step, giving you the structure and confidence to respond effectively when鈥攏ot if鈥攁n incident occurs.
The Core Phases of an Effective Response
Once you've got your incident response team in place, it鈥檚 time to talk about the plan itself. This is where the rubber meets the road. A solid response isn't a single frantic action; it's a series of methodical, coordinated phases. Each one has its own goals, challenges, and critical decisions. Moving through these stages step-by-step is what prevents panic and ensures you don't miss anything crucial.
When a breach hits, the first few moments are pure chaos. Having a clear, phased approach turns that chaos into a structured process. It lets your team focus on fixing the problem instead of scrambling to figure out what to do next.
This graphic breaks down the typical flow professionals follow, from the initial alarm bell to getting systems back online and keeping everyone in the loop.
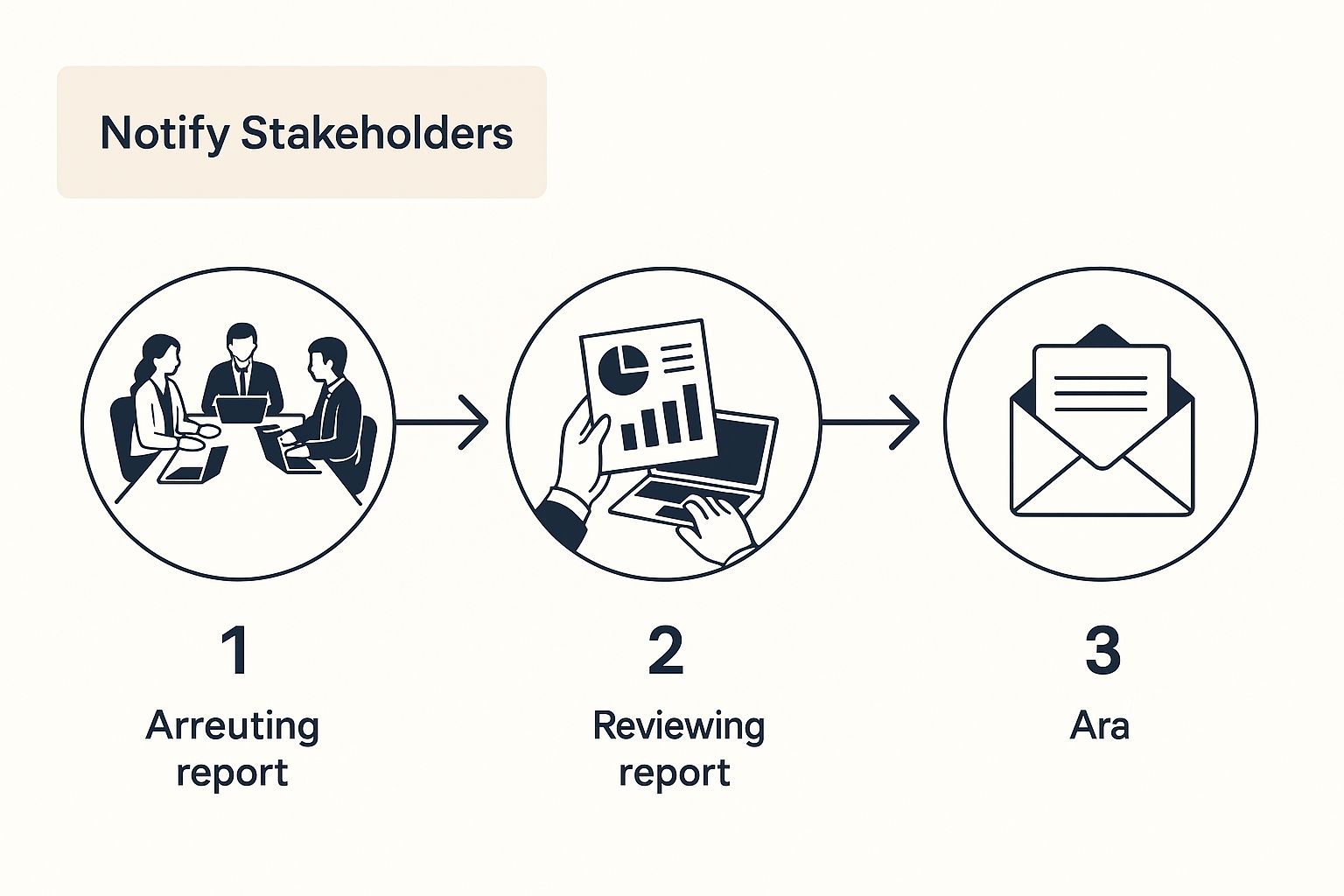
What I like about this visual is how it shows stakeholder communication isn't just a final step. It's a parallel track that runs alongside all the technical work from start to finish.
Detection and Analysis
You can't fight what you can't see. The first phase, Detection and Analysis, is all about spotting that something is wrong and figuring out just how bad it is. This part is a race against the clock, especially since attackers could have been quietly sitting in your network for weeks or even months.
An incident can pop up on your radar in a few ways:
- An automated security tool throws an alert about weird network traffic.
- An employee reports a sketchy email or notices their computer acting strangely.
- An outside party, like a customer or even law enforcement, gives you a heads-up about a potential data leak.
Once something is flagged, the real analysis begins. Your tech lead has to quickly determine if it鈥檚 a false alarm or the real deal. They鈥檒l be asking the tough questions: What systems are hit? What data is on the line? How did they get in? This initial triage is what shapes the rest of your response.
Don鈥檛 get bogged down trying to find every little detail right away. The goal here is to get just enough information to make smart decisions for the next phase鈥攃ontainment.
Containment and Eradication
Okay, you've confirmed it's a breach and you have a rough idea of the damage. Now, you have to stop the bleeding. The Containment and Eradication phase is about boxing the attacker in, limiting the damage, and then kicking them out for good.
Containment is a tricky balancing act. You'll face a huge decision: do you isolate a few affected machines or pull the plug on the whole network? A targeted approach is less disruptive, but a full shutdown might be your only option to stop a fast-moving ransomware attack in its tracks.
For instance, if one department's file server is compromised, you might get away with just taking that server offline. But if you see malware spreading across critical systems like wildfire, taking the entire network down might be the only way to save it.
After containment, you move to eradication. This means systematically scrubbing every trace of the attacker from your environment. That could involve:
- Removing malware from every infected device.
- Disabling any user accounts they compromised.
- Patching the security holes the attackers used to break in.
You have to be absolutely thorough here. If you miss a single backdoor, the attackers will be right back in, and you鈥檒l have to start all over again.
Recovery and Restoration
With the threat gone, it鈥檚 time to get back to business. The Recovery and Restoration phase is all about bringing your systems back online safely and getting operations back to normal. Trust me, it鈥檚 not as simple as just flipping a switch.
You have to restore from clean, verified backups that you know predate the incident. If you accidentally restore from a compromised backup, you鈥檒l just reintroduce the malware and undo all your hard work. As each system comes back online, it needs to be monitored like a hawk to make sure it鈥檚 stable and secure.
This is also your chance to implement stronger security controls based on what you learned. If they got in through a weak password, now's the time to roll out multi-factor authentication everywhere. If they exploited a server you forgot to patch, you need to lock down your patch management process. The goal is to come back stronger. For a closer look at the nuts and bolts of this process, check out these .
Post-Incident Activity
The fire is out, but you鈥檙e not done yet. The final phase, Post-Incident Activity, is arguably the most important for your long-term health. This is where you conduct a full post-mortem to figure out exactly what happened, what you did right, and what you could鈥檝e done better.
This is a no-blame review. The point is to learn from the painful experience and harden your defenses. You'll want to document a complete timeline of the incident and pinpoint any gaps you found in your tech, your processes, or your team鈥檚 training.
This phase is more critical than ever. Recent stats show that system intrusions are now the cause of more than half of all data breaches, a huge jump from 36% just a year ago. On top of that, 22% of breaches started with stolen credentials, often targeting remote access tools. These numbers scream for response plans that not only contain threats fast but also include a deep-dive analysis afterward to fix the root cause.
The insights you gain here feed right back into your data breach response plan, creating a loop of continuous improvement. Every incident鈥攚hether real or just a drill鈥攕hould make your plan stronger and your team sharper for the next one.
Managing Communications and Legal Duties
Once your tech team gets the immediate threat under control, the crisis isn't over. It just shifts into a new, equally tough phase. The spotlight moves from firewalls and code to people and trust. This is where you have to juggle the complex world of communications and legal duties that can make or break your company's recovery.
Getting this part right isn't about technical skills. It鈥檚 all about transparency, strategy, and empathy. The goal is to control the narrative, meet your legal obligations, and begin the hard work of rebuilding the trust you've lost.
Navigating the Legal Labyrinth
The second a breach is confirmed, a legal clock starts ticking. And it ticks fast.
Data breach notification laws are a messy patchwork that changes wildly depending on where your customers are and what kind of data you lost. Regulations like GDPR in Europe and state laws like the California Consumer Privacy Act (CCPA) have strict, non-negotiable reporting deadlines. You simply can't ignore them.
Under GDPR, for example, you generally have just 72 hours from the moment you find out about a breach to notify the right authorities. Miss that window, and you're looking at staggering fines. In the U.S., there's no single federal law, so you might have to deal with the requirements of dozens of different state laws at once.
This is exactly why having legal counsel on your response team isn't a luxury鈥攊t鈥檚 an absolute must. They鈥檙e the ones who will guide you through the critical questions:
- Who do we have to tell? This could be anyone from regulatory bodies and the affected individuals to credit reporting agencies.
- What exactly do we need to say? Notifications usually require specific details about the breach, the data involved, and what you鈥檙e doing about it.
- What's our deadline? Your legal team will keep track of all the different timelines to make sure you're fully compliant.
Remember, your website's privacy policy is a promise you made to your users about their data. During a breach, that document gets put under a microscope. To make sure your policies are solid from day one, it's crucial to understand the importance of having a privacy policy long before an incident ever happens.
Crafting a Clear Communication Strategy
While your lawyers are focused on compliance, your communications lead needs to manage how you talk to the world. Frankly, how you communicate during a crisis can do more damage to your reputation than the breach itself. A botched announcement can wipe out years of customer loyalty in just a few hours.
The key here is to be proactive, transparent, and consistent. Your communication plan, which should be a core part of your overall data breach response plan, needs to have pre-approved templates and talking points ready to go for different groups.
In a crisis, silence is interpreted as guilt or incompetence. A swift, honest, and empathetic message shows you are in control and respect your customers, which is the first step toward rebuilding trust.
Your communication strategy has to speak to several key audiences:
- Your Internal Team: Your own people should hear the news from you first, not on the evening news. Give them a clear, factual rundown and tell them exactly how to handle questions. Arming them with the right information stops rumors and keeps your message unified.
- Affected Customers: This is your most important audience. Your notification needs to be simple, jargon-free, and straight to the point. Tell them what happened, what data was involved, what you're doing to fix it, and what they can do to protect themselves (like changing passwords).
- Business Partners and Vendors: Keep your partners in the loop, especially if the breach could affect their business or data.
- The Public and Media: Get a concise, factual press statement ready. Pick a single spokesperson to handle all media questions. This keeps your message consistent and prevents things from getting twisted.
Learning from Real-World Communication Failures
History is full of companies that completely fumbled their breach response, making a bad situation a whole lot worse. The Bank Sepah of Iran breach, which exposed over 42 million customer records, was a masterclass in what not to do. The bank first denied it, then later admitted it, completely destroying public trust.
Likewise, the Oracle Cloud breach impacting 140,000 organizations showed how a vulnerability in a third-party service can create a massive ripple effect. It drove home the point that clear, timely communication is essential for everyone in the supply chain.
These incidents teach a hard lesson: trying to hide or downplay a breach never works. The truth always comes out, and the damage from a perceived cover-up will be far worse than the damage from the breach itself. A successful response is all about owning the situation with honesty and showing a real commitment to making things right.
Keeping Your Response Plan Battle-Ready
A data breach response plan isn't a document you create once, file away, and forget about. Think of it more like a living strategy that needs to be constantly tested, sharpened, and updated. A plan that looked rock-solid six months ago could be full of holes against today's threats. Keeping it battle-ready is what separates a truly resilient company from one that's just checking a box.
This process of continuous improvement is how you build organizational muscle memory. When a real incident hits, your team won't be scrambling to read the plan for the first time. They鈥檒l be executing a series of actions they've already walked through, turning potential panic into a calm, measured response.
More Than Just a Fire Drill
The only way to know if your plan actually works is to put it to the test. This means running regular drills that simulate a real-world security incident. Let me be clear: these exercises aren't about passing or failing. They are about finding the weak spots in your strategy before a real attacker does.
You can approach this in a few different ways, from simple tabletop discussions to much more involved simulations.
- Tabletop Exercises: This is the most common place to start. Get your incident response team in a room and walk them through a fictional breach scenario鈥攎aybe a ransomware attack or a phishing incident that compromised executive credentials. Talk through each phase of your plan and have team members explain exactly what they would do.
- Full-Blown Simulations: These are far more intensive and mimic a live attack as closely as possible. Your technical team will respond to a simulated threat in a controlled environment, really testing their tools and processes under pressure. This gives you priceless insight into your actual detection and containment capabilities.
The goal of any drill is to make mistakes in a safe environment. Every gap you find in a simulation is a potential disaster you've just prevented in the real world.
Reviewing and Refining Your Playbook
After every drill鈥攁nd especially after every real incident鈥攖he most crucial step is the post-mortem. This has to be a no-blame review where the entire response team gets together to analyze what happened. You need to be brutally honest about what went well, what completely fell apart, and why.
This review shouldn't be a casual chat; it needs to be structured and thorough. Document a complete timeline of the events and pinpoint specific areas for improvement.
Key Questions for Your Post-Mortem:
- How quickly did we actually detect the simulated threat?
- Were roles and responsibilities crystal clear to everyone involved?
- Did our communication plan work the way we thought it would?
- Did we hit any technical or procedural roadblocks that slowed us down?
The answers to these questions become your action items. They feed directly back into your data breach response plan, creating a powerful loop of continuous improvement. Maybe you discovered your emergency contact list was outdated, or that a key piece of software failed under pressure. These are the insights that harden your defenses over time.
This proactive approach is tightly linked to your overall security posture. Testing your response plan is, in essence, a practical form of risk management. A foundational step in this process involves understanding your vulnerabilities, which you can explore further in our guide to a risk assessment for small business. It鈥檚 all part of the same commitment to preparation.
Ultimately, a plan that is regularly tested and updated transforms from a static document on a server somewhere into a dynamic and effective tool. This commitment to readiness is what truly prepares your organization to face a security crisis with confidence and control.
Common Questions About Data Breach Response
Even with a solid guide in front of you, putting together your first data breach response plan can feel like a huge task. It鈥檚 only natural to have a few questions pop up as you try to turn these ideas into a real-world strategy for your own company.
Let鈥檚 tackle some of the most common things that trip people up. Getting clear answers here will give you the confidence to build a plan that actually works when you need it most.
How Soon Do I Need to Report a Data Breach?
This is probably the most urgent question you'll ever have to ask, and the answer isn't simple. It completely depends on where you operate and what kind of data was exposed. There鈥檚 no single, universal deadline, which is exactly why having legal counsel on speed dial is non-negotiable.
For instance, if you fall under Europe's GDPR, the clock starts ticking immediately. You've generally got just 72 hours from the moment you discover a breach to get the proper authorities in the loop.
Back in the United States, it鈥檚 a lot murkier. We don't have a single federal law, so you鈥檙e left navigating a patchwork of state-level rules. Reporting timelines can be anything from a vague "as soon as possible" to hard deadlines of 30 or 45 days. Your legal team has to map out the specific requirements for every single place you do business.
Don鈥檛 guess on reporting deadlines. Seriously. The penalties for getting this wrong are steep. This is a core reason you have a legal expert on your incident response team.
What Is the Biggest Mistake Companies Make?
Honestly? Bad communication. It trips up more companies than any technical failure. In a panic to protect their reputation, they delay telling anyone, put out vague statements, or try to downplay how bad things really are. This almost always blows up in their face, destroying customer trust and leading to much worse financial and reputational fallout.
Internally, the biggest mistake is not having clearly defined roles. When a crisis hits and no one knows who鈥檚 in charge of making the tough calls, you get chaos. That indecision burns through precious time your tech team needs to stop the bleeding. A well-rehearsed plan with a clear chain of command is your best defense.
Does My Small Business Really Need a Response Plan?
Yes. Absolutely. 100%. Cybercriminals love targeting small and medium-sized businesses because they (correctly) assume security is weaker. An SMB is far more exposed to the fallout from a breach.
For a small business, a major data breach can be a true extinction-level event. You likely don鈥檛 have the cash reserves to swallow massive regulatory fines, expensive lawsuits, and the wave of customers who will leave after a poorly handled incident.
Your plan doesn't need to be as complicated as what a giant corporation uses, but it has to cover the fundamentals: how you'll spot a breach, contain it, notify the right people legally, and talk to your customers. Just having a documented plan shows you've done your due diligence, which can soften the blow significantly if an attack ever happens.
Navigating the legal minefield of a data breach is tough, but you don't have to figure it out alone. Cordero Law specializes in providing the strategic legal counsel businesses need to prepare for and respond to security incidents. We empower you with the knowledge to protect your business and maintain trust.
Learn how Cordero Law can help you build a resilient legal framework for your business.
