Protecting your trade secrets isn't a one-and-done task. It requires a layered strategy combining robust legal agreements, smart technical safeguards, and consistent operational habits.
Think of it like building a fortress. Your contracts are the walls, technology creates the locks, and your daily security practices are the vigilant guards. A single weak point can compromise everything.
What Every Business Owner Needs to Know First

Before you start drafting complex legal documents, let's get clear on what a trade secret actually is. It’s any piece of confidential information—from a secret recipe to a detailed customer list—that gives your company a competitive edge.
Unlike patents, which require you to publicly disclose your invention, a trade secret’s value lies entirely in its confidentiality. This means protecting it is an active, ongoing process, not a one-time registration. This guide will serve as your roadmap, breaking down the essential pillars of an effective defense system.
Why Trade Secret Protection Is More Important Than Ever
Lately, protecting trade secrets has become a critical focus for businesses. With recent judicial changes sometimes limiting what can be patented, many companies—especially in tech and software—are finding that trade secrets offer a more attractive and flexible intellectual property strategy.
This legal shift really underscores the need for a solid protection plan. For a closer look at these trends, check out the insights on the .
Choosing the right IP protection is a big decision, and understanding your options is key. For a deeper dive, check out our guide comparing the pros and cons of a trade secret vs patent.
The Three Pillars of Trade Secret Protection
An effective strategy isn't about choosing just one method. It's about integrating three core components that work together to secure your most valuable assets. These three pillars—Legal, Technical, and Operational—form the foundation of a comprehensive trade secret defense.
Let's break down what each of these pillars involves.
| Pillar | Primary Tools | Key Goal |
|---|---|---|
| Legal Agreements | NDAs, Confidentiality Agreements, Employee Handbooks | Create legally binding obligations to maintain secrecy with anyone who has access to your information. |
| Technical Safeguards | Encryption, Access Controls, Network Monitoring | Prevent unauthorized digital access and data breaches through technological security measures. |
| Operational Habits | Clean Desk Policies, Secure Document Disposal, Employee Training | Build a security-conscious culture where protecting information is part of everyone's daily routine. |
By weaving these three elements into your business operations, you create a powerful, multi-layered defense that makes it incredibly difficult for your confidential information to fall into the wrong hands. Each pillar supports the others, ensuring no single point of failure can bring down your entire system.
Building Your Legal Fortress

While good habits and digital security are important, your legal agreements are the absolute bedrock of your trade secret protection strategy. A simple, downloaded template just won't cut it.
To truly shield your secrets, you need a web of contracts that are specific, enforceable, and custom-fit to every single relationship your business has—from employees to partners to contractors. Think of it as a series of interconnected walls, each designed to safeguard your information from a different angle.
Crafting Ironclad NDAs
A weak Non-Disclosure Agreement (NDA) is worse than having no NDA at all. Why? Because it gives you a false sense of security. The most common mistake I see is making them too broad or vague. Courts often toss out agreements that don't clearly define what, exactly, is considered confidential.
Saying something generic like "all business information" is a recipe for disaster. It’s unenforceable. A strong NDA needs to get specific, listing out the categories of information being protected. For a great primer on the fundamentals, you can get a better understanding of the basics of an NDA to make sure your agreements are solid from the start.
To make your NDAs truly effective, make sure they include these critical clauses:
- Specific Definition of Confidential Information: Don't be shy. Detail the types of information, like "customer lists," "marketing strategies," "software source code," and "financial projections."
- Clear Purpose for Disclosure: State exactly why the information is being shared (e.g., "for the purpose of evaluating a potential business partnership"). This limits how they can use it.
- Duration of Confidentiality: Specify how long the obligation to keep the information secret lasts. This should extend well beyond the end of the business relationship.
- Return or Destruction of Information: Require the other party to return or securely destroy all confidential materials when you ask or when the agreement ends.
Beyond the NDA: Integrating Protection Everywhere
Your legal defenses have to extend into every single contract that touches your intellectual property. Each agreement is a fresh opportunity to reinforce your security and legally bind people and companies to protect what's yours.
Take a freelance software developer, for instance. Their contract needs to go way beyond project deadlines and payment terms. It must include strong confidentiality clauses and, critically, state that all work product—the code, discoveries, everything—is the exclusive property of your company. This simple step prevents them from turning around and reusing your proprietary code for their next client.
A trade secret doesn't have to be physically stolen to be misappropriated. A former employee who simply remembers your customer pricing strategy and uses it at their new job can be in violation. This is why strong exit procedures and ongoing confidentiality duties are so essential.
Securing the Employee Lifecycle
Your employees are your greatest asset and, frankly, your biggest risk when it comes to trade secrets. Protection has to start the day they're hired and continue right through their departure.
During Employment: Your employment agreements should clearly spell out the employee’s duty to protect company secrets. This isn't just a formality; it’s a legal tool that sets clear expectations from day one.
Upon Departure: The exit interview is your last line of defense. This is where you formally remind departing employees of their ongoing legal obligations under the agreements they signed. Have them sign a document confirming they have returned all company property—laptops, phones, documents, and digital files—and have not kept any copies. This creates a clean paper trail and dramatically reduces your risk down the road.
Creating a Culture of Security

Legal documents are important, don't get me wrong. But they're only half the battle. Without practical, on-the-ground security habits, even the tightest contracts can fall apart. This is where building a security-conscious culture becomes your best defense in the fight to protect your trade secrets.
A culture of security isn't about making everyone paranoid. It’s about making smart, protective actions second nature for every single person on your team. When protecting sensitive info becomes a reflex instead of a chore, you've built a powerful human firewall.
Implement Simple, High-Impact Policies
You don’t need a ridiculously complex rulebook to see a huge difference. Simple, consistent habits can slash your risk of accidental leaks. These are the building blocks of a secure workplace.
Start with these fundamentals:
- Document Labeling: Put a clear system in place for marking sensitive documents. Simple labels like "Confidential" or "Internal Use Only" act as immediate red flags, telling employees this information needs special care and can't just be shared with anyone.
- Clean Desk Policy: This is about more than just being tidy. A clean desk policy means everyone secures sensitive documents, laptops, and drives when they step away from their desks. It’s a dead-simple rule that stops casual snooping or opportunistic theft in its tracks.
Just picture a consulting firm where a visitor glances over and sees a competitor’s sales projections left on a desk. That single slip-up can shatter trust and cost a fortune, all because of a messy workspace.
Lock Down Physical Access And Disposal
Your physical office can be just as vulnerable as your digital one. Controlling who comes and goes—and how you get rid of sensitive materials—is a critical piece of the puzzle.
Think of it like this: a surprisingly common source of data breaches is stuff just being thrown in the trash. A competitor digging through your company's garbage—a classic tactic known as "dumpster diving"—is a very real threat.
To shut this down, invest in cross-cut shredders for all sensitive paperwork. When it comes to digital media, make sure old hard drives and USBs are either physically destroyed or professionally wiped clean before you toss them.
Make Security A Shared Responsibility
Ultimately, your security culture lives or dies with your team's buy-in. You need to shift the mindset from a top-down mandate to one of shared ownership. Everyone has to understand their role in protecting the company’s crown jewels.
Run regular training sessions that use real-world examples to make the risks feel tangible. Explain why these policies matter—how protecting a client list or a new product design directly impacts the company's success and, by extension, everyone's job security.
For a deeper dive, there are some excellent that can help turn your employees into your strongest defenders. By making security a team effort, you empower your people to be vigilant, proactive, and truly invested in protecting your most critical assets.
Mastering Your Digital Defenses
In today's world, your biggest business vulnerabilities are almost always online. Legal agreements and secure office habits are crucial, but without strong digital defenses, you're leaving the front door wide open for hackers and even malicious insiders. A huge part of protecting your trade secrets is mastering the technical tools that shield your data.
This isn't about becoming a cybersecurity expert overnight. It's about putting a few powerful, non-negotiable measures in place to build a formidable digital wall around your company's most valuable information, whether it’s sitting on a server, floating in the cloud, or saved on an employee's laptop.
The Principle of Least Privilege
One of the most effective strategies you can adopt is the principle of least privilege. It’s a simple concept: give employees access only to the information they absolutely need to do their jobs, and nothing more.
Your marketing intern doesn't need the source code for your flagship product. Your sales team shouldn't be able to peek into sensitive R&D files. By limiting access, you dramatically shrink your risk. An accidental data leak or a compromised employee account can only damage a small, contained area instead of exposing the entire company. Think of it as a foundational step in preventing internal leaks, which are often the most damaging.
Must-Have Digital Security Measures
Once you have your access controls sorted, the next step is to layer on specific technologies that actively guard your data. These aren't just "nice-to-haves"—they are the essential locks and alarms for your digital assets.
Data Encryption: This is your data's first line of defense. Encryption basically scrambles your information, making it unreadable to anyone without the right key. All sensitive data, whether it's stored on servers (data at rest) or being sent via email (data in transit), must be encrypted.
Multi-Factor Authentication (MFA): Passwords alone just don't cut it anymore. MFA requires a second form of verification—like a code from a phone app—before granting access. This simple step can block over 99.9% of automated cyberattacks. It's a game-changer.
Network Monitoring: Think of this as your digital security camera system. Monitoring tools track data flow and user activity, flagging suspicious behavior. For instance, it can alert you if an employee suddenly starts downloading huge quantities of files at 2 AM.
These measures form a powerful trio for safeguarding your digital information. The chart below gives a great visual of how these key defenses are being adopted and their real-world impact.
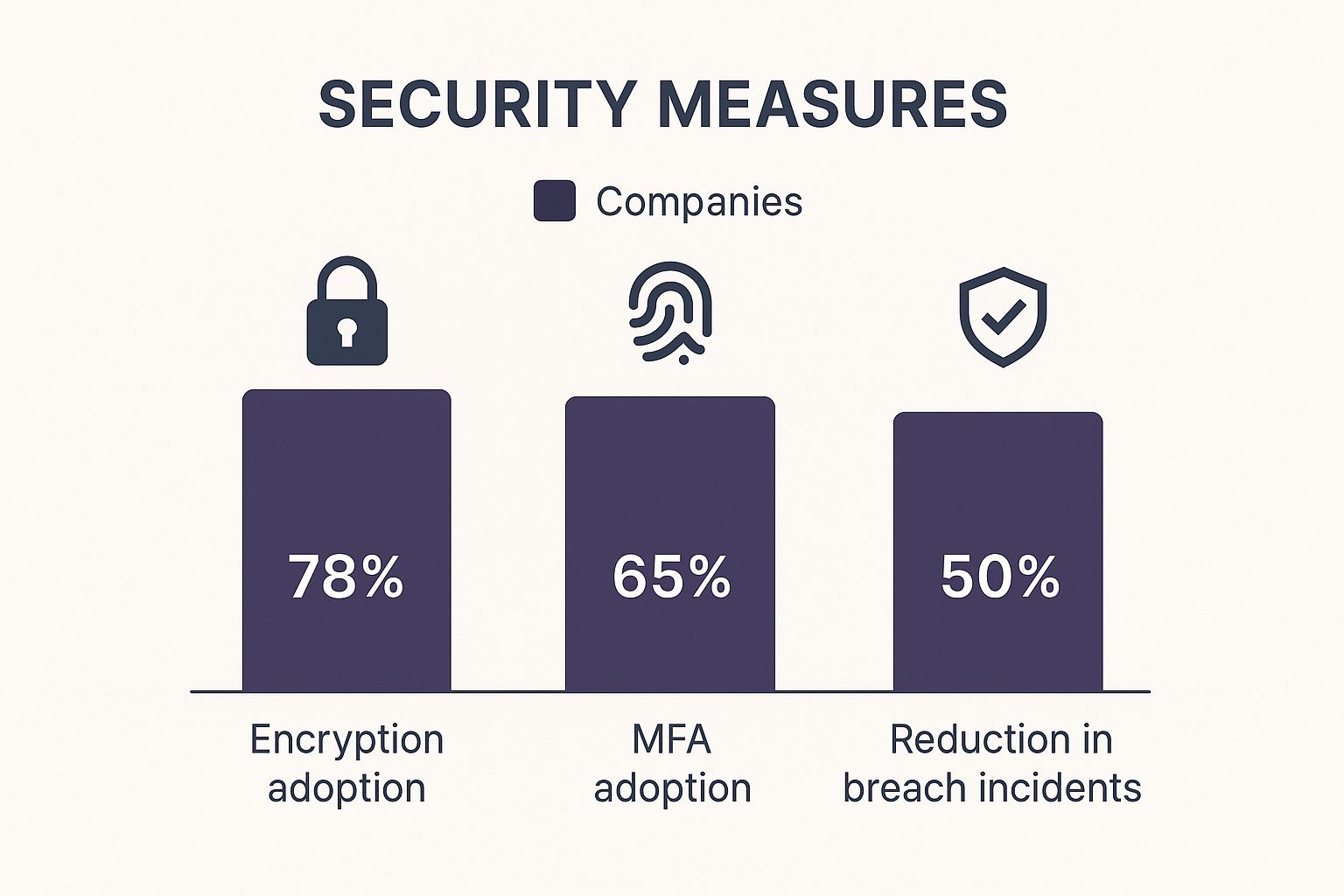
As you can see, while encryption is becoming standard practice, there's still a big gap in MFA adoption—a measure proven to dramatically cut down on breaches.
To put these concepts into a clearer context, let's break down some essential cybersecurity measures.
Essential Cybersecurity Measures for Trade Secrets
| Security Measure | What It Does | Primary Threat Mitigated |
|---|---|---|
| Data Encryption | Scrambles data to make it unreadable without a decryption key. | Unauthorized access to stolen data (both at rest and in transit). |
| Multi-Factor Authentication (MFA) | Requires a second form of ID beyond a password to log in. | Compromised or stolen employee passwords. |
| Access Control (Least Privilege) | Limits user access to only the specific files and systems they need. | Insider threats (malicious or accidental) and lateral movement by hackers. |
| Network Monitoring | Continuously scans network traffic for unusual or malicious activity. | Data exfiltration, malware infections, and internal policy violations. |
| Endpoint Security | Protects individual devices (laptops, phones) with antivirus and firewalls. | Malware, phishing attacks, and threats from unsecured personal devices. |
Implementing these controls in tandem creates a layered defense that is much harder for any single threat to penetrate.
Your digital security is only as strong as its weakest link. A single employee using a weak password without MFA on a personal device to access your cloud server can undermine millions of dollars in other security investments.
Navigating Cloud and BYOD Risks
The convenience of cloud services and "Bring Your Own Device" (BYOD) policies also introduces new risks. Your trade secrets are no longer confined to your office walls; they're spread across third-party servers and personal devices.
Before you trust any cloud vendor with your data, do your homework. Scrutinize their security protocols, data encryption standards, and how they handle user access controls. Make sure your contract clearly states that you retain full ownership of your data. For companies developing unique applications, understanding the nuances of software IP protection is especially critical when you're working with external platforms.
And if you let employees use personal devices, you absolutely must have a strict BYOD policy. This policy should mandate security measures like device encryption, strong passwords, and the installation of company-approved security software. By setting and enforcing these digital rules of the road, you can protect your trade secrets no matter where they are.
Securing Secrets in a Remote and Global World
Protecting your company’s crown jewels was a lot more straightforward when everyone clocked in under one roof. But now, with distributed teams scattered across the country and partnerships spanning the globe, the old boundaries have vanished. And the risks have exploded.
Knowing how to protect trade secrets isn't just a local issue anymore; it's a global challenge.
Expanding your business overseas or collaborating with international partners opens up incredible opportunities, but it also means you’re playing in a different legal ballpark. Due diligence is absolutely non-negotiable. Before you even think about signing a contract, you have to get a handle on the intellectual property enforcement environment of the country you’re dealing with.
Unfortunately, trade secret protection isn't the same everywhere. The USTR's 2025 Special 301 Report is a real eye-opener here. It shows just how inconsistent enforcement can be, with some countries offering far weaker legal options than others. The report even has a "Priority Watch List" of nations with serious IP concerns. It's essential reading. You can find more details about these global IP enforcement challenges.pdf) directly in the report.
Fortifying Your Remote Workforce
Your team working from home introduces a whole new set of variables. Personal Wi-Fi networks, shared apartments, and the use of personal phones or laptops can all create weak spots if you don't manage them. This is where a clear, enforceable remote work security policy becomes your best friend.
This isn’t about micromanaging. It’s about setting up smart guardrails that protect both your employees and the company. The goal is to get as close as you can to your office's security level, no matter where your team is logging in from.
A huge mistake I see companies make is assuming their standard employee agreement covers the unique risks of remote work. It doesn't. You absolutely need a dedicated policy that spells out expectations for home network security, device management, and secure communication.
Here are a few practical things to build into your remote work security checklist:
- Mandatory VPN Usage: This one is non-negotiable. Require every employee to connect through a secure Virtual Private Network (VPN) anytime they access company systems. This encrypts their internet traffic, making it gibberish to anyone snooping on an insecure home or public network.
- Secure Wi-Fi Configurations: Don't just hope for the best. Give your team clear, simple instructions for locking down their home Wi-Fi. This means using strong WPA3 encryption, changing the default router password (you'd be shocked how many people don't), and maybe even setting up a separate guest network for all the non-work smart speakers and TVs.
- Company-Issued Devices: Whenever you can, give your employees company-owned laptops. This is a game-changer. It gives you control over security updates, what software gets installed, and data access, slashing the risks that come with personal devices.
As more and more of our work moves to cloud platforms for storage and collaboration, knowing the right security measures is critical. You can find some excellent, detailed advice on leveraging these to lock down your data in a distributed world. By adapting your strategy for a modern, decentralized workforce, you can make sure your most valuable secrets stay that way—secret.
Common Questions About Protecting Trade Secrets
Trying to get your arms around intellectual property can be a headache, but figuring out the key differences is your first move toward building a solid protection plan. I find that most business owners are wrestling with the same core questions. Let's clear them up so you can make confident decisions.
What Is the Difference Between a Patent and a Trade Secret?
This really boils down to one thing: public disclosure versus confidentiality.
A patent is powerful. It gives you an exclusive monopoly over your invention for about 20 years. But there's a trade-off. To get that protection, you have to file a detailed application that lays out exactly how your invention works for the whole world to see. It becomes public knowledge.
A trade secret, on the other hand, can be protected forever—as long as you can keep it a secret. If your innovation is something a competitor could easily reverse-engineer just by looking at the final product, a patent is probably your safer bet. But if your asset is a process, a formula, or a killer client list that you can reliably keep under wraps, a trade secret offers much more lasting power.
What Counts as Reasonable Steps to Protect a Secret?
There's no magic, one-size-fits-all checklist from the courts on this one. What's considered "reasonable" really depends on your industry, the size of your company, and just how valuable the information is.
That said, a strong, defensible strategy always includes a few key pieces:
- Consistent Use of Legal Agreements: This is non-negotiable. It means using NDAs and confidentiality clauses in every single contract with employees, contractors, and business partners. No exceptions.
- Digital Security Measures: You need to have basic safeguards in place. Think tiered access controls (so people only see what they need to see), data encryption, and multi-factor authentication.
- Physical and Operational Controls: Don't forget the simple stuff. This means physically labeling sensitive documents, restricting access to key areas of your office, and actually training your team on your security policies.
When it comes down to it, courts are looking for a documented, consistent effort. They want to see that you didn't just call it a secret; you actively treated it like one.
A common mistake is thinking a trade secret has to be some complex technical formula. The truth is, a well-curated customer list, a unique pricing strategy, or even a list of reliable suppliers can all qualify for protection—if you’ve taken the right steps to keep them confidential.
An Employee with Access to Secrets Is Leaving. What Now?
Okay, this is a critical moment. You need to act methodically and immediately. A sloppy exit process is one of the fastest ways for your trade secrets to walk right out the door.
First, conduct a formal exit interview. This isn't the time for accusations. It's a professional and necessary moment to remind the departing employee of the ongoing confidentiality obligations they agreed to when they signed their employment contract.
Next, get it in writing. Have them sign a document confirming they've returned all company property. That means physical items like laptops, phones, and keys, and just as importantly, digital assets (confirming they've deleted any local files).
Finally, the second they are officially off the clock, their access to everything must be shut down. Email, cloud platforms, internal servers, software—everything. This swift, documented process is your best defense against problems down the line.
Navigating trade secret law requires more than just good policies; it demands expert legal guidance. At Cordero Law, we partner with entrepreneurs and innovators to build a legal fortress around their most valuable assets. If you're ready to secure your competitive edge, visit us at to learn how we can help.
